Directive Blogs
What Your Business Can Learn From the Recent Twitter Social Engineering Hack
This may be an uncomfortable truth when it comes to data security: the weakest link to keeping your data secure will be your employees. As social media giant Twitter recently discovered, despite the best technical security measures you have in place, all it takes is a break in protocol to place your client’s data and your business’ reputation at risk.
Twitter Suffers One of the Most Public Hacks Ever
On August 15, 2020, the Twitter accounts of several high-profile people, including Joe Biden, Barack Obama, Kanye West, Bill Gates, Jeff Bezos, and Elon Musk, were compromised. There were around 130 tech giants, celebrities, and political figures who were compromised in the attack. Across all of these widely popular accounts, messages went out requesting users send money, and the result of the hack was the loss of at least $100,000 from Twitter users who fell for it.
The hackers opted for a “smash and grab,” which means that they got their money and disappeared. It could have been much, much worse, as Twitter struggled to regain control. Think about it for a moment: they had access to a primary communication resource for some of the most influential people in the world; people whose statements can shape public opinion, the stock market, and even politics. It’s almost fortunate that all they did was trick some users out of money.
Your Data is Valuable, So is Your Brand
Imagine if instead of hacking Apple’s Twitter feed to ask for money, the hackers posted that Apple was going to buy another company or discontinue the iPad or even post an inappropriate message? Once they gained access to the accounts, they were free to post anything. The hackers could have easily wreaked havoc to the reputations of the accounts they gained access to. They could have posted a link to ransomware that could infect every computer on a network. The widespread damage would have been massive.
Even if the tweets were eventually proven to be fraudulent, it wouldn’t have been before customers, vendors, and the market would have reacted poorly. Worse, even after the post is removed, there’s a real possibility some of your customers may lose faith in your ability to keep their data secure if you can keep your own secure. This is an issue Twitter is now facing. Always remember, the Internet never forgets.
While we are aware that some businesses still treat their social media as an afterthought (or worse, treat it with disdain) it is simply too powerful to ignore.
Where Does Social Engineering Come In?
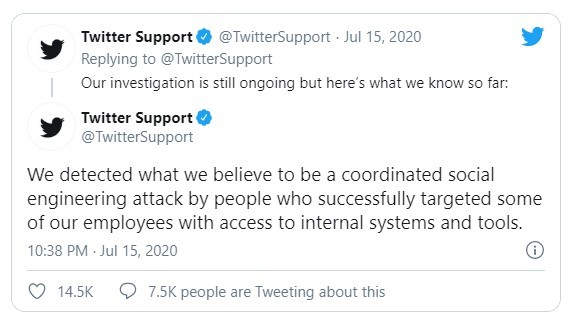
Twitter stated that the company detected what they believed to be "a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools."
What this means is that there wasn’t a group of hackers trying to “break” Twitter’s network security, as often displayed in popular media. In actuality, they used social engineering tactics to convince a Twitter team member to grant them access to user credentials.
Whereas Hollywood depicts hackers sitting in a dark room in front of screens with green matrix code scrolling by, some of the most devastating hacks are caused by negligence or betrayal. Social engineering tactics typically involve a user who has a level of access getting tricked into sharing that access.
While there is still conflicting information as to whether the success of the social engineering attack was due to human error or a willing accomplice, one thing is sure, someone was given a level of privileges they shouldn’t have been granted, and that is what allowed user security to be compromised. Now is the time to enact best practices for your access management.
The Weakest Link to Your Data’s Security is Your Team
We know it’s difficult to accept, but even if you have the most advanced data security system, one that is highly resistant to brute force attacks, it can all be undone due to a team member clicking on the wrong link. That’s all it takes for your system to become compromised.
When we look at what happened to Twitter, we see that the hackers understood they couldn’t brute force their way into Twitter’s database, so they used social engineering to trick someone into granting them access. Social engineering works, and it will be used on your team and your business by hackers. It probably already is, in some form or another. The only way to prevent social engineering attacks from being successful is to take the time to train your team.
Social Engineering Can Target Anyone
While it seems that social engineering attacks are focused on famous people or enterprise-level businesses, such as Twitter or the CEO of Apple, the reality is social engineering is a tactic, not a philosophy. Every business, regardless of its size, and every person, irrespective of their fame, is fair game. We’ve even seen this happen locally, to a local Oneonta grandmother. The biggest mistake many small to medium-sized businesses make is thinking that they aren’t of interest to a cybercriminal.
In today’s increasingly connected business environment, SMBs are often linked to larger organizations. If an SMB’s data gets compromised, there’s also the possibility that they will provide hackers with a door into the larger business’ data. Data security is vital to all businesses regardless of their size. All doors, no matter how small, need to be locked.
Why is Social Engineering Effective?
Social engineering is effective because it takes advantage of a person’s natural tendency to either be helpful or to be afraid. Social engineering uses four basic tactics to trick your team into providing access to your business data.
- User Carelessness: Your team simply doesn’t follow best data security practices, including poor password management.
- Perceived Helpfulness: A member may get a password reset request and give the distressed person the credentials, without verifying their validity.
- Working Within the Comfort Zone: A team member may receive what appears to be a legitimate email from a recognized email account causing them to become comfortable, forget their training and release sensitive information.
- Fear Tactics: A team member may receive an email which appears to be from your tech department (or other authority figure) requesting they take an action or risk consequences.
Three Lessons Learned From The Twitter Hack
The social engineering attack on Twitter certainly caused a seismic shift in regards to how social media security is viewed. It was a shock to the system and a wake-up call regarding the trustworthiness of companies that handle our data. Yet despite the uncertainty, there is some value to be learned from the experience. Here are some takeaways from the hack that you can apply to your business to better secure it against a similar social engineering attack.
- Pay attention to and monitor your social media. The longer the hack is allowed to run, not only does the damage grow more significant, but it becomes more difficult to regain control of your data. You must be agile enough to respond quickly.
- Ensure you have a viable back-up in place and ready to go. Unfortunately, sometimes hackers may have wormed themselves so deeply into your system, that the only way to remove them is to delete your data and start fresh. If you are concerned about your ability to ‘wipe your hard drive,’ then your business will most likely be unable to survive a cyberattack.
- Communicate with your team, vendors, and clients if there has been a data breach. While it is embarrassing to admit your data has been compromised, it‘s far better than having your client’s accounts end up on the dark web. Worse still is finding the account used to post inappropriate statements on social media, damaging their and, of course, your brand. When you communicate with your clients, you give them the ability to protect themselves by changing their credentials or even monitoring their credit, if need be.
Note: Many states have strict requirements for data breach notification, along with extensive financial penalties, if your business is found non-compliant.
You Need Your IT to Be Properly Managed, and as Secure as Possible
As we have seen, social media can be a double-edged sword. With it, you can directly communicate with your friends, family, clients, team, and vendors alike, but like all swords, you have to be mindful where you swing it. If you aren’t confident in your ability to manage your online presence or need a little help, our Ultimate Social Media Rig can help you master social media networking and marketing.
One of the most important steps you can take to protect your data is to have the ability to abandon it and start fresh from an uncompromised backup at any time. When you have a BDR (backup and disaster recovery) in place, you have the peace of mind to face any disaster (natural or man-made) knowing you can be up and running in no time.
Managed IT can provide a wealth of services and solutions for your business regardless of its size. Moreover, as we have seen, the company's size is no safeguard against being targeted for a cyberattack. When you outsource your technology to proven professionals such as Directive, you reduce the chance of your data being compromised, or your technology failing. You also increase your ability to adapt to the new normal, such as support of the sudden interest in developing a remote workforce.
The goal of Managed IT is to provide your business with the room to grow by allowing you to focus on increasing your bottom line. For more information on how Managed IT can help your business, download our FREE whitepaper, which discusses the 10 Benefits Managed IT can bring to your business or call 607-433-2200 today to schedule an appointment.
Comments


